Our solution
PT Anti-APT detects and prevents targeted attacks. It enables detecting attacker presence on the network with maximum speed and recreating a full picture for thorough investigation.
Thwart black hats: PT Anti-APT detects attacks on Active Directory
Active Directory is often the main prize for APT groups. Threat actors constantly find new vectors for targeting AD and not all security vendors are able to keep pace.
PT Anti-APT successfully detects attacks on Active Directory as well as other lateral movement attempts to expand from a network beachhead.
Protects against the most important threats
At the core of the solution is a unique knowledge base, which is regularly supplemented based on our pentesting, investigations of complex incidents, and security testing of various systems. Awareness of real-world tactics, techniques, and procedures plus Positive Technologies expertise offers a decisive advantage when confronting even the newest threats.
Key features
Foil phishers: PT Anti-APT detects packed and encrypted malware
For attackers, phishing is the main way in to government organizations. That's why this method is used by 87 percent of APT groups during the initial phase of the kill chain. To evade detection by antivirus software, they deliver it to infrastructure with packing and encryption (techniques known as "Obfuscated Files or Information" and "Software Packing"). Our solution is able to spot malware even when hidden with these techniques.
Shortens response time and accelerates investigation
Understanding context is crucial: PT Anti-APT stores raw traffic, key session parameters, and detailed behavioral descriptions of scanned malware. Experts use this information to rapidly find traces of compromise, detect attackers as they move around the network, and devise countermeasures.
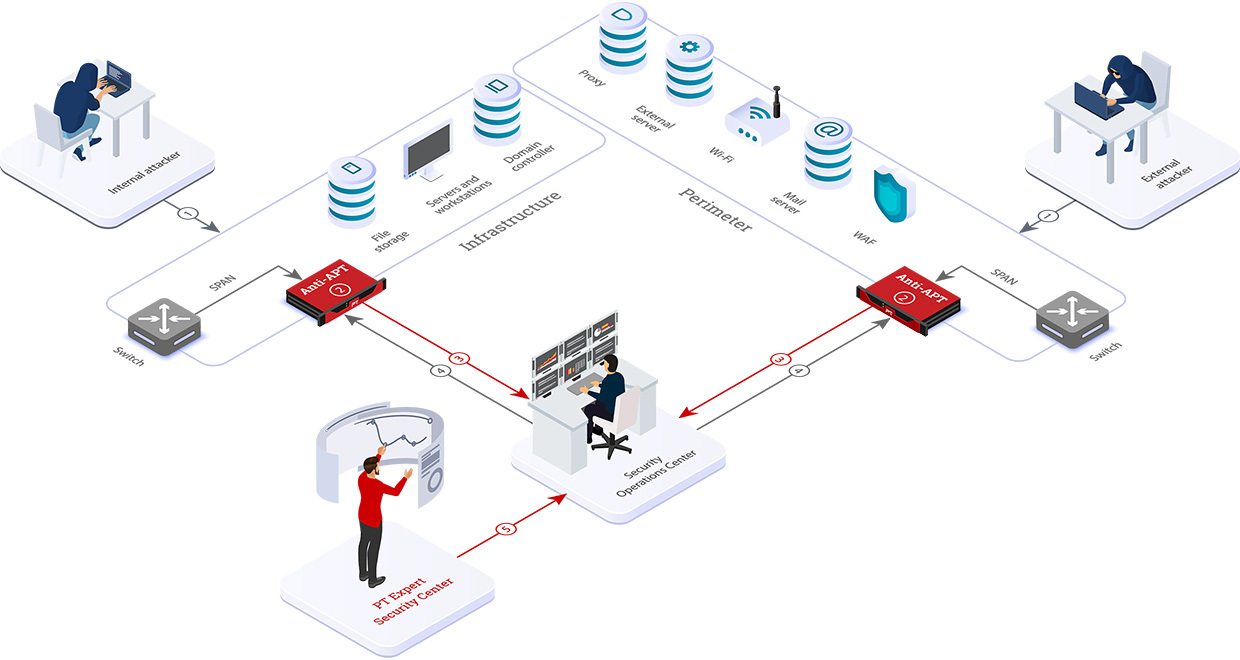
How it works

Data stays inside
All data regarding attacks and scanned objects is stored on the infrastructure of the client company on-premises. This data never leaves the network perimeter. Because of reduced spread of information about attacks and damage, this approach minimizes reputational risks.